Which of the Following Best Describes an Email Security Gateway
A with external access. Which of the following are functions of gateway.

What Is Email Security Definition Benefits Examples Best Practices Toolbox It Security
An individual hacks into a military computer and uses it to launch an attack on a target.

. Prevention of Layer 7 attacks. The connection is not authenticated. A security analyst wants to harden the companys VoIP PBX.
In the Email Following term describes the contents of the message. Email security gateways- This type prevents the transmission of emails that break company policy or will transfer information with malicious intent. A white-hat hacker is a good guy who uses his skills for defensive purposes.
Ability to perform packet filtering. Which of the following describes how access lists can be used to improve network security. VoIP trunk gateways - This type.
Sophos Central Admin shows features under their product names such as Endpoint Protection. Theres also an Overview that amalgamates the features for all of your. A gateway that does not connect to.
A stateful firewall cannot authenticate users or prevent. A stateful firewall performs better than a proxy server. Enterprise Networking Security and Automation Version 700 Modules 3 5.
Of the following security zones which one can serve as a buffer network between a private secured network and the untrusted internet. One of the first best practices that organizations should put into effect is implementing a secure email gateway. A Trojan Horse.
IPsec is often installed on todays IPv4 networks to protect communication over VPN networks. Solutions for Chapter 2B Problem 14MCQ. Which of the following best describes the primary security issue with null sessions.
It is used to access VPN as well as between VPNs. An access lists filters traffic based on the IP header or information such as source or destination. Question 146 Topic 1.
The sessions are not terminated properly. It monitors emails that originate from an organization. The proxy server is also called.
It allows an individual or organization to protect the. Which of the following best describes an exclusive gatewaya. We can control network traffic to resources in a virtual network using a network security group.
The analyst is worried that credentials may be intercepted and. The IT department is reporting that a company web server is. A Denial of Service attack.
A subject B cc C to D contents. Az network nsg create is used to create a network security group. A proxy server is a computer that acts as a gateway between a users computer and the Internet.
The only gateway in a BPMN diagramb. Email security refers to the collective measures used to secure the access and content of an email account or service. A subject Abbrivation of SMTP is.
Whether its sophisticated nation-state attacks targeted phishing schemes business email compromise or a ransomware attacks such attacks are on the rise at an. All email security gateways have the ability to quarantine or block email that contains detected malware phishing attacks spam as well as other malicious content. Which of the following BEST describes an email security gateway.
An email gateway scans and processes all incoming and outgoing email and. It accepts mail and forwards it to other mail servers.
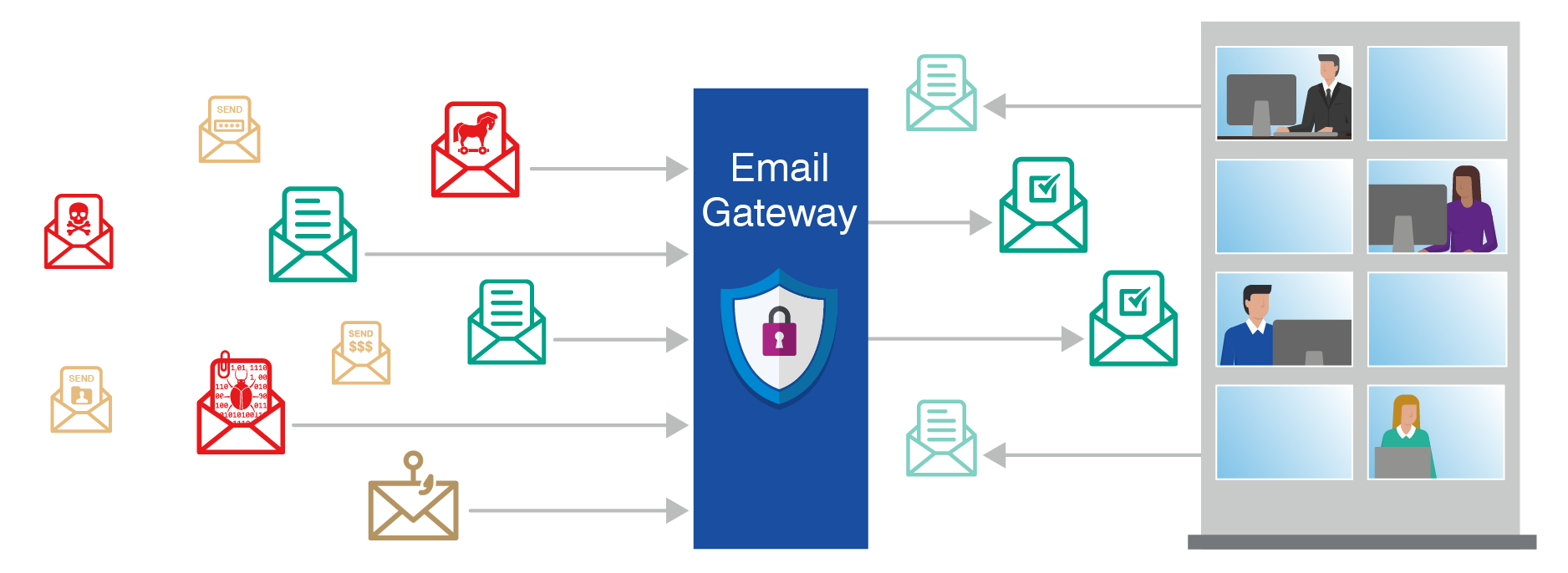
What Is Email Security Meaning Best Practices More Proofpoint Uk

What Is Email Security Definition Benefits Examples Best Practices Toolbox It Security

What Is Email Security Definition Benefits Examples Best Practices Toolbox It Security

Comments
Post a Comment